
Prof. David Vernon (Course Director)
School of Informatics
University of Skövde
Sweden
david vernon.eu
vernon.eu
Objectives | Content | Instruction | Assessment | Work Profile | Feedback | Notes | Links | Timetable
Course Objectives
The goal of this course is to impart an understanding and working knowledge of the theoretical foundations of a representative range of the constituent sub-disciplines of informatics.
This involves the study of the scientific method, modelling methodologies, core theories, and fundamental techniques, and their application in the analysis and design of computer-based information systems.
In the process, the course seeks to instil an appreciation of how theory influences practice in creating effective, efficient, and useful people-centred computer-based information systems.
Upon successfully completing the course, a student will have achieved the following learning outcomes and will be able to:
- Explain the scientific method of problem abstraction, hypothesis formation and test, experimentation, and analysis;
- Explain the distinction between modelling methodology and instances of specific theories and models;
- Explain the difference between descriptive and normative models;
- Apply a working knowledge of a representative sample of core theories and fundamental techniques in informatics, in general, and in computational, cognitive, and socio-technical systems, in particular;
- Compare and contrast competing theories and complementary techniques in the context of typical computer-based information systems.
Course Content
The broad area of computing is traditionally broken down into different functional sub-disciplines such as computer engineering, computer science, software engineering, information systems, and information technology.
Informatics takes a different approach, dealing with the design and development of systems that provide information for individuals, organizations, and society in a timely, effective, and efficient manner. It focusses on how this information is represented, processed, and communicated in natural and artificial systems. As a result, it treats the various facets of computing as a cohesive whole, addressing it from three complementary perspectives:
1. Computation
2. Cognition
3. Socio-technology
The computation perspective deals with the usual mathematical and engineering issues that are needed to design and implement a given computer application.
The cognition perspective deals with how people & computer systems solve problems, make decisions, and learn.
The socio-technology perspective puts both of these together in the context of organization: it focuses on the ways people can leverage benefit from the information in these systems in support of their organizational goals.
Each of these perspectives draws on a broad body of knowledge and principals that can be categorized under three headings:
1. Modelling methodologies
2. Core theories
3. Fundamental techniques
Modelling methodologies address the scientific method and the manner in which scientific theories are formed, formulated, and adopted. It doesn’t address any specific scientific domain but it does influence what a theory can and cannot claim.
Core theories (e.g. complexity theory in computational systems or organizational theory in socio-technical systems) address particular domains but in a manner that has general applicability.
Fundamental techniques are more focused on specific methodologies, mechanisms, and algorithms for bringing about a required result within any given core theory. They provide a way of realizing a given computational theory, for example, in explicit terms that can subsequently be implemented as an operational information system.
This course covers twelve theories/techniques, four from each of the three perspectives of informatics. These are described in Appendix 1 of the Course Handbook.
Student Instruction
Students on this course are drawn from many different backgrounds in computing and have a minimal amount of shared knowledge. Given the diversity of the material to be taught, it is likely that each student will be challenged in different ways.
In order to ensure that no student falls behind early on, the course will increase the rate of learning progressively. To achieve this, the course begins with an introduction to informatics as a discipline and then presents an overview of the material that comprises the remainder of the course. It then progresses to a more detailed treatment of each topic individually, and finishes with an in-depth treatment of certain topics on a student-by-student basis.
The first three phases are implemented through classroom instruction (lectures and seminars); the fourth phase though individual supervision.
The nature of informatics as a team-based discipline is also reflected in the delivery, having the students work in groups in seminars and assignments so that they learn how to collaborate effectively. Since peer assessment and review is also an important and pervasive process in today’s workplace, relevant exercises also included in the seminars and tutorials.
Lectures
Sixteen lectures, each lasting one hour and forty-five minutes, are scheduled for formal teaching. One lecture is allocated to an introduction to informatics. Two lectures are allocated for the top-level overview of all course material.
One lecture is allocated to modelling methodologies. Four lectures are allocated to core theories and fundamental techniques in each of the three perspectives of informatics: computation, cognition, and socio-technology. Here is a timetable for the delivery of the course, showing the time allocated to lectures, seminar, tutorials, and assessment.
Since this course addresses the interplay between theory and practice, the introductory lecture will address the practical essentials of informatics: its purpose and domain of operation, its component disciplines, the basic concepts of data and information, the system development lifecycle, and how theory supports practice in various aspects of this lifecycle.
The two lectures that provide the top-level overview of all course material are critically important for the students. They give the students an explanatory preview of what material they will be exposed to and they provide an opportunity to show how the material relates to the course objectives, the learning outcomes, and how the material fits together in one coherent whole.
Seminars
There are six seminars, two for each perspective: computation, cognition, and socio-technology. Each seminar will comprise two halves, one for each of the two topics covered in that perspective in the previous week (or, occasionally, the week before that).
Prior to each seminar, the students work in small groups on an exercise set at the end of each topic lecture. Typically, this exercise will assess the use of a particular theory or technique in a given application domain. Alternatively, it might be a comparative analysis of two or three complementary theories or techniques, based on a small amount of supplementary reading (typically a tutorial article, review, or survey). The goal is to provide the students an opportunity to assess different approaches based on the material covered in the lectures and to generate a synthesis of their relative strengths and weaknesses in a given context.
Assuming a class size of 24 students, eight groups of three students will be formed. Four groups will be selected during the seminar, two for the first seminar topic and two for the second.
During the seminar, each of the selected groups will make a presentation on the exercise announced in the topic lecture. After each presentation, there will be a short class discussion, moderated by the instructor. This provides a way of allowing the students to validate each other’s understanding and refine it as a result of the feedback from classmates and the instructor.
It is important to emphasize that the seminar is a learning exercise, not an assessment one. Nonetheless, to ensure that all students engage fully in the seminars, all groups, whether they were selected or not to give their presentation, must hand up a printed copy of the two presentations they prepared for each seminar. Those who fail to do so will be targeted for selection in subsequent seminars.
Student Assessment
The degree to which the student achieves the required learning outcomes of the course is assessed through an assignment and a case study. Of the 7.5 hp course load, 2.0 are allocated to the assignment, 5.0 hp to the case study, and 0.5 to an oral presentation on the case study.
Assignment
The assignment focuses on the use of informatics in a selected application domain, addressing all three perspectives in the body of knowledge: computation, cognition, and socio-technology. The goal of the assignment is to select and justify appropriate modelling methodologies, core theories, or fundamental techniques required for the effective deployment of a solution strategy in all three aspects of computation, cognition, and socio-technology in a given application area. This is a horizontal theoretically-oriented study, targeting a comprehensive treatment of some information system. The assignment is conducted as a group project. Groups will be formed with a view to ensuring that members of a group have complementary backgrounds.
Here are the assignment and marking scheme and here are the assignment skeleton report and guidelines.
Case Study
The case study provides the student with an opportunity to use the material they have learned in the course in the analysis and appraisal of a computer-based information system in a more challenging context than the assignment. It complements the assignment in that it addresses a narrower spectrum of issues in just one of the perspectives of informatics, but it does so at a deeper level by assessing two or more possible modelling methodologies, core theories, or fundamental techniques. Thus, the case study is a vertically-oriented investigation in contrast to the wider-ranging horizontal investigation associated with the assignment.
Specifically, given a selected application domain, the case study performs a critical appraisal and comparative analysis of two or more competing or complementary solutions strategies (modelling methodologies, core theories, or fundamental techniques) drawn from the body of knowledge in informatics and deployed in either the computational, cognitive, or socio-technical aspect of that application area.
The assignment and the case study are naturally complementary, with the latter providing an opportunity for more detailed analysis and focussing on just one of the three complementary perspectives of informatics rather than all three. In contrast to the assignment, the case study is carried out individually rather than in a group.
The student is expected to produce a printed report for the case study. The student may reuse any of the work for the assignment in the report.
The case study poses some interesting problems in striking the right balance between the needs and capabilities of M.Sc. and Ph.D. students, both of whom will take this course. While both M.Sc. and Ph.D. students will need to conduct some independent investigation when writing the case study report, it is conceivable that Ph.D. students will align the topics of their case study with the topics of their research. However, the assessment of the case study does not focus on the quality or extent of the research (the student is going to get a Ph.D. for that) but will focus instead on the critical appraisal of the various modelling methodologies, core theories, and fundamental techniques as they relate to the informatics problem being investigated in the case study.
Here are the case study and marking scheme and here are the case study skeleton report and guidelines.
Presentation
The purpose of the oral presentation is to convey the main findings in the case study in an accessible, instructive, and engaging manner.
It is mandatory for every student to attend the presentations. As many members of staff as possible should also attend. This will provide students with an opportunity to engage well-founded principled debate with their peers on the work they have done in their respective case studies
The allocation of marks for the presentation is included in the case study and marking scheme.
Grading
Students are awarded one of three grades: a pass with distinction (VG), pass (G) or a fail (U).
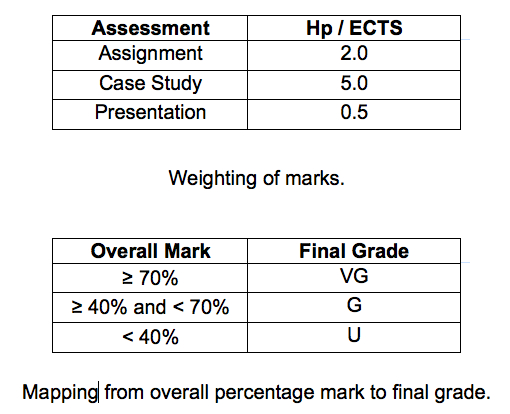
To facilitate consistent marking, a standard marking scheme is used for both assignment and case study. Furthermore, the case study will be marked by two people: the supervisor and a second-reader. The final mark is the average of the two marks, provided they do not differ by more than a given amount (10%). In that case, a third reader may be asked to mark the report. A formal procedure for handling such a situation is set out in the case study and marking scheme.
Work Profile
A balance must be struck between the time allocated to formal instruction, delivered through direct contact with members of staff in lectures and seminars, and independent study, supported by members of staff outside formal course contact hours. Furthermore, the amount of material to be delivered needs to be scoped appropriately to ensure adequate coverage at the required level of detail in the available time. As already noted, the course is delivered at a 25% pace with total of approximately 200 hours of study.
An explicit allowance of time for self-study is made in the course delivery. One hour of self-study is allocated for every lecture hour. Three hours of self-study are allocated for every seminar hour to allow adequate time for preparation.
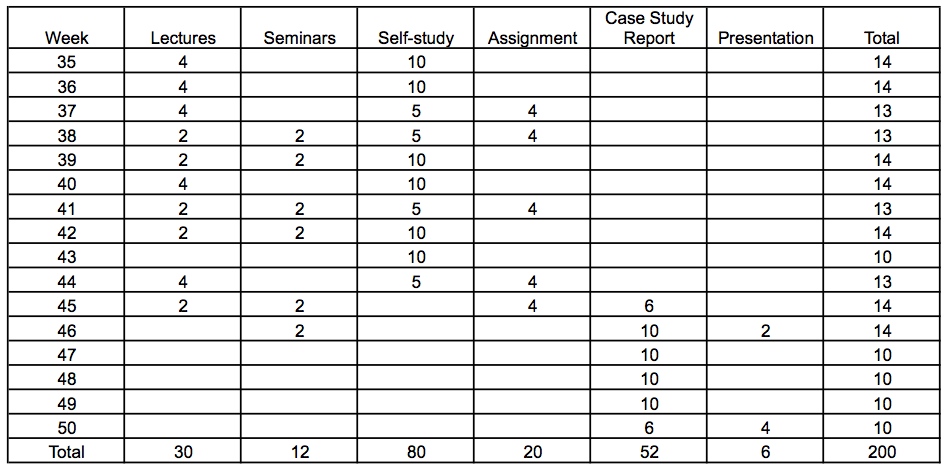
A typical work profile is shown in below. As noted above, this is based on the assumption that one two-hour lecture is devoted to an introduction to the course, two lectures to a top-level overview of all the course material, one lecture to modelling methodology, and four lectures in each of the three perspectives of informatics (computation, cognition, and socio-technology). This gives a total of 16 lectures and 32 contact hours. In addition, six two-hour seminars are included: two for each perspective, giving a total of 12 contact hours. Six tutorials are included at the end of the course to address concerns students may have about the course material. Allowing one hour of independent study for each lecture hour and three hours of preparatory study for each seminar hour, the total amount of time devoted to formal instruction is 126 hours. The remaining time is allocated to the assignment, case study, and presentations, in approximate proportion to their loading of 2.0 hp, 5.0 hp, and 0.5 hp.
Feedback and Quality Assurance
The course content, student instruction, student assessment, and work profile are subject to on-going scrutiny and improvement. The input for this quality assurance process is a student questionnaire to be completed by each student periodically each semester.
Notes
Schedule of Lectures, Seminars, and Tutorials
Timetable
Lecture Notes
Lecture 01 - Overview & Introduction to Informatics
Lecture 02 - Preview of Course Material
Lecture 03 - Modelling Methodology
Lecture 04 - Complexity Theory
Lecture 05 - Automata Theory and Computability Theory
Lecture 06 - Discrete Probability and Information Theory
Lecture 07 - Algorithmic Strategies
Lecture 08 - Paradigms of Cognitive Science
Lecture 09 - Cognitive Architectures
Lecture 10 - Decision Theory
Lecture 11 - Embodied and Social Cognition
Lecture 12 - Organizational Theory
Lecture 13 - Management Theory
Lecture 14 - Games
Lecture 15 - Innovation
Seminar Exercises
Exercises - Complexity Theory
Exercises - Automata Theory and Computability Theory
Exercises - Discrete Probability
Exercises - Algorithmic Strategies
Exercises - Serious Games
Assignment
Assignment
Assignment Skeleton Report and Guidelines
Case Study
Case Study
Case Study Skeleton Report and Guidelines
Links
Supplementary Reading
A Brief Guide to the System Development Lifecycle
Barbacci 1998 - Architecture Trade-off Analysis
Bechara, Damasio, and Damasio 2000 - Emotion, Decision Making, and the Orbitofrontal Cortex
Hanson 2005 - Decision Theory
Morgan 1998 - Images of Organization
Movellan 2008 - Introduction to Probability Theory
Platt and Glimcher 1999 - Neural correlates of decision variables in parietal cortex
Schneider 2012 - Information Theory Primer
Course Documentation
Course Handbook
Course Plan IT706A
Kursplan IT706A
Student Questionnaire
Curricula
ACM Curricula Recommendations
Ethics
IEEE Code of Ethics
IEEE Computer Society Software Engineering Code of Ethics
Course Director & Examiner
David Vernon